Identifying Office 365 Phishing attempts
Identifying Office 365 Phishing attempts https://www.missingpixel.co/wp-content/uploads/2019/11/Phish-Hero-1024x743.jpg 1024 743 Russ Russ https://secure.gravatar.com/avatar/b0a23be87fc9d646956183c8ef7670cf?s=96&d=mm&r=gHow to catch a Phish.
Phishing has evolved from the more obvious forms of spam email, and without doubt has become much more targeted, personalised and a lot more effort goes into the production of content, essentially to dramatically increase the possibility of their success.
As with some of the examples listed in our previous article, the real aim now is not to gain the odd sale from bulk email such as the prolific Viagra email from back in the day, but instead to obtain personal information, specifically financial information, with the ultimate goal being to extract money using various methods from the recipient by deceit.
A side effect of spam and Phishing email becoming more sophisticated is that it becomes much more difficult to prevent it from appearing in a user’s inbox. Historically, you could create rules to automatically delete suspicious emails using keywords and phrases that would commonly appear in the subject or body of rouge emails, or of course to block emails from certain domains or senders, or automatically block emails with certain attachment types. In most cases, modern Phishing emails are particularly clever in the way that they are produced, and do not contain obvious phrases that can be targeted to block them, indeed they are also often from spoofed addresses (made to look like they have been sent from the email address of a genuine, recognisable email account).
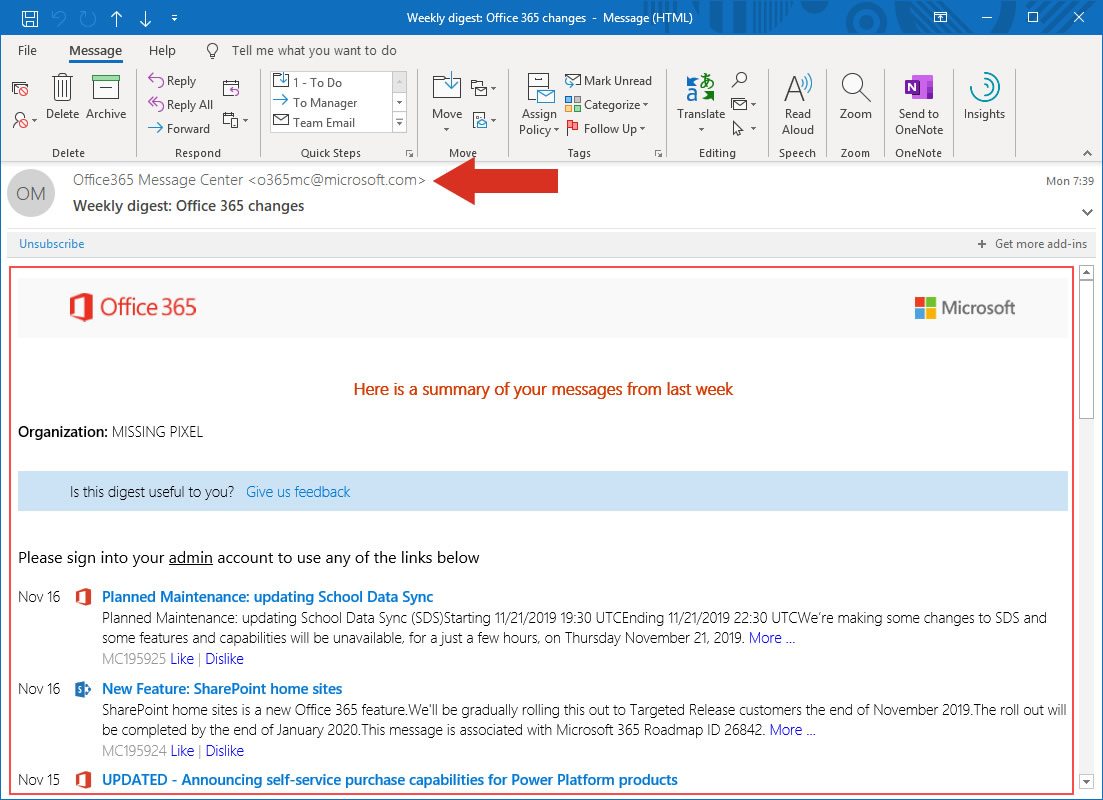
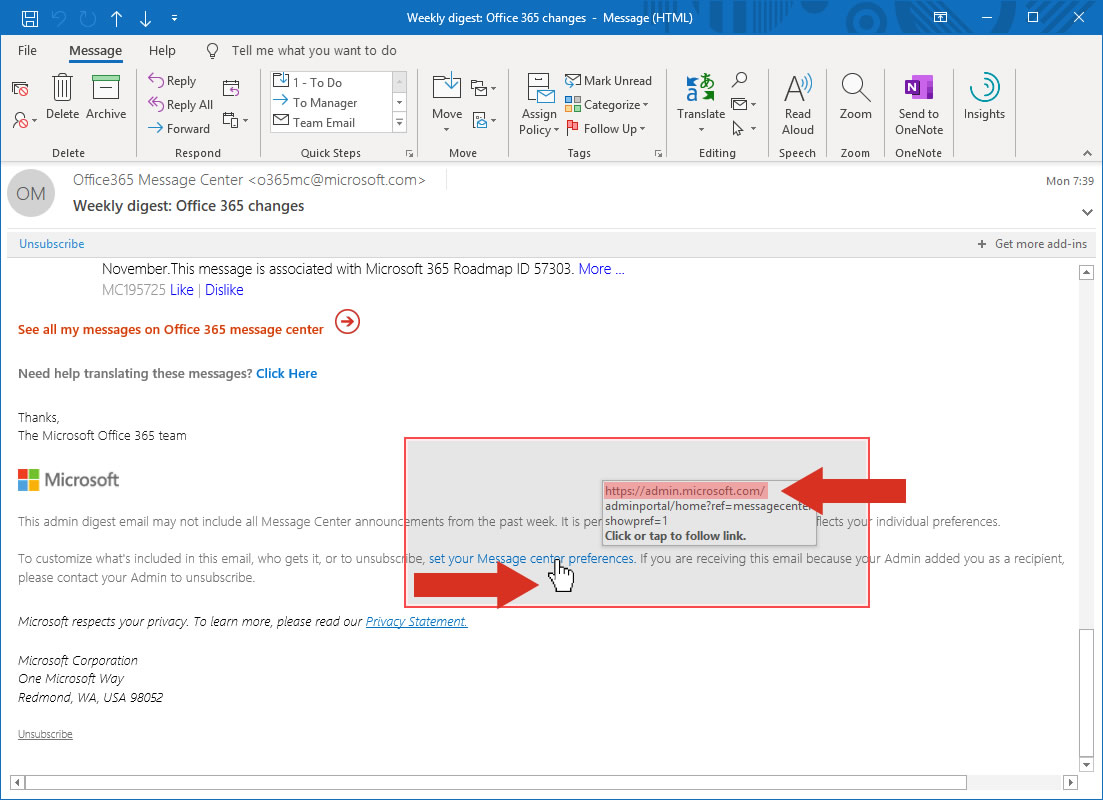
The two example images above are genuine Microsoft emails, the message content is well formatted, contains official looking graphics and logos, and the sender email address appears to come from a genuine domain (microsoft.com). Additionally, within the content of the email there are several links, one of which is highlighted in the second image – inspecting the popup closely (which tells you where you will be redirected to if you click on the link), you can see that actioning this particular link will take you https://admin.microsoft.com.
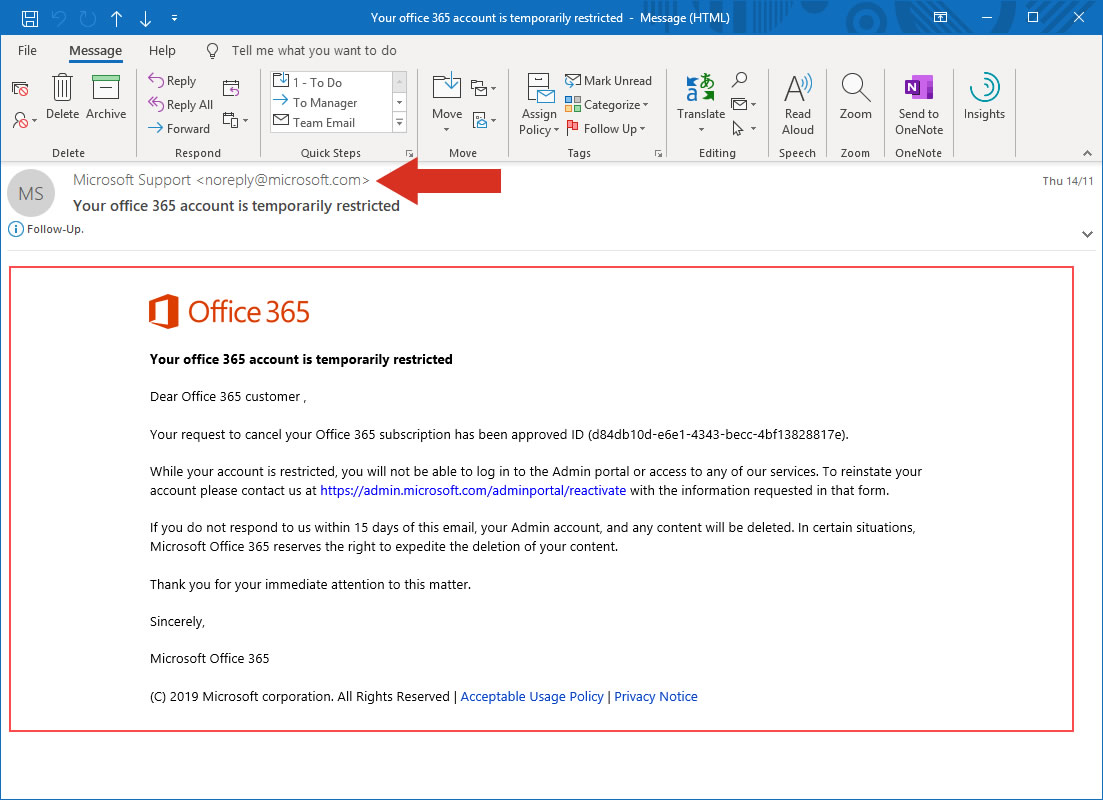
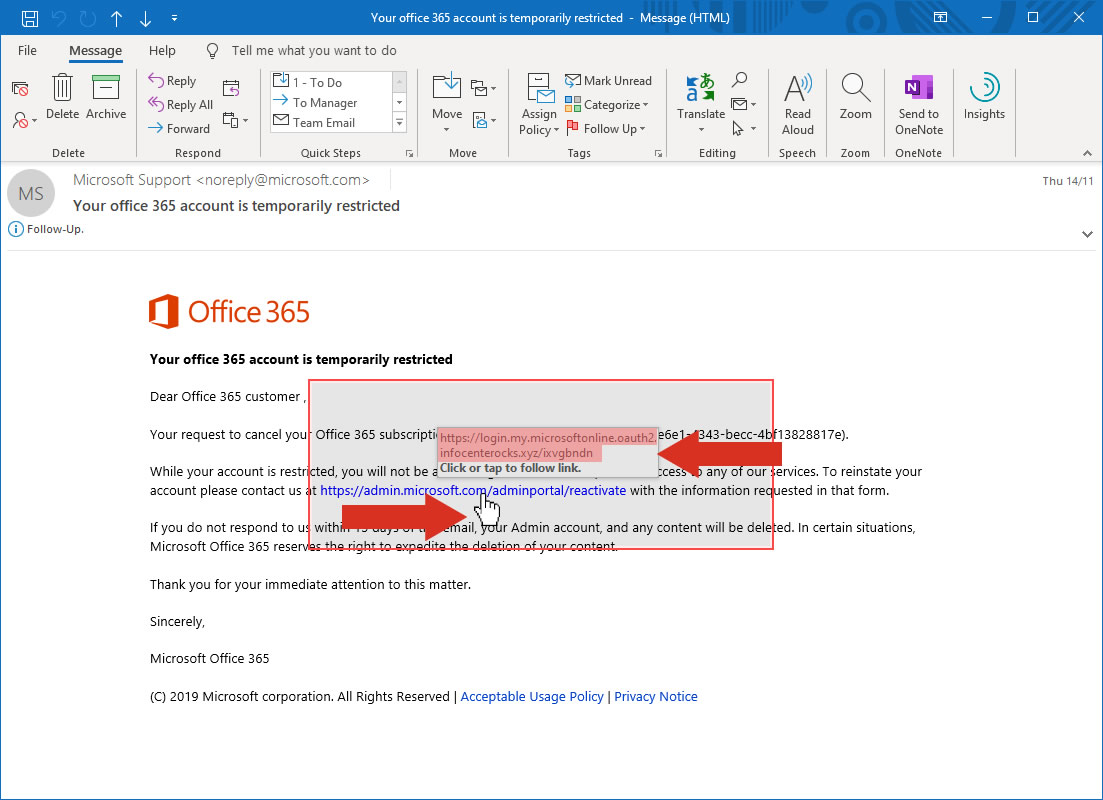
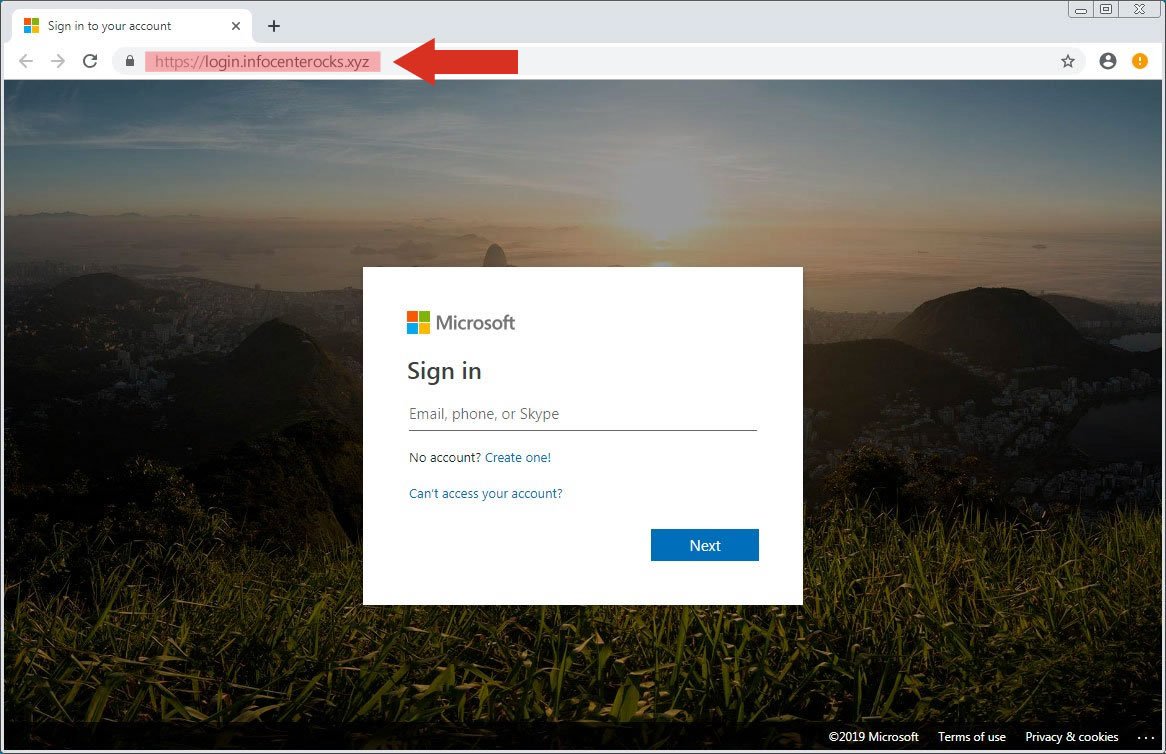
The two example images below are from a Phishing email, and a very convincing one too. The content look genuine (no obvious issues with language, spelling etc.), it contains official looking graphics and logos, and also appears to have come from a genuine domain (microsoft.com). The only giveaway on this email is the destination you’d be sent to by clicking on the link it’s requesting that you action (infocenterocks.xyz.com) – even though the link text in the email suggests that it will take you to microsoft.com/adminportal/reactivate. You could understand a user clicking on the link in this email and actioning the content, especially as the email suggests that all of your data will be deleted if you don’t!
The final image above shows the destination page arrived at by clicking on the link in the Phishing email. The only thing here that’s out of place is the URL in the address bar (highlighted) – the rest of the page again looks completely genuine and mimics exactly the genuine Microsoft account login page. You could quite innocently enter your username and password into the login box here, and you’d probably get redirected to another page that might say something like ‘Congratulations, you’ve now reactivated your account’ – when what you’ve actually done is just given away your username and password for your Microsoft account to someone who can cause some real issue for you!
The main points of advice we can offer to assist in spotting, and of course helping to prevent you from becoming the victim of a Phishing attack can be found below. As part of our product portfolio, we offer various additional mailbox and security products that help minimise the volume of Phishing emails received, and also additional protection for user email accounts to prevent unauthorised access and use of usernames and passwords should they ever inadvertently be revealed or exposed as a result of actioning any content within bogus emails. We’ll also be making a guide available, so that you’re able to circulate amongst employees/colleagues so that users will have information on the latest trends and be able to help protect themselves from Phishing attacks
We’ve heard some real horror stories of how people have been affected by sophisticated phishing attacks, and in most cases it’s been completely forgivable that users have responded to requests as the content quality, layout, sender address and links can seem absolutely genuine.
How can you identify Phishing emails?.
- Check the sender address, if they are claiming to be from a particular company does their email address suggest that?(1)
- Check the quality of the language used in the email – most poorly produced Phishing emails are not particularly well written and may contain ‘speeling’ mistakes or poorly constructed ‘centanses’. 😊
- Is there anything particularly suspicious about the content – what are they requiring you to do, think why they would be asking you to action something.
- Have you ever communicated with the sender before, are they using different language to that which they’ve used previously? Are they requesting anything strange or out of character?
- When you hover over any links in an email, do they look like they will take you to a genuine, recognisable webpage, or does the link suggest that it may take you somewhere unrecognisable.
- If an email contains a link or an attachment, what does it suggest it’s for? If it claims to be an invoice, are you expecting one? Be particularly wary of .htm, .zip and other strange files.
- Are you actually expecting communication from this sender? If you’re not expecting a Zip file from bill.gates@hotmail.com then it’s probably not a genuine email.
- If anything looks suspicious, and you’re able to, contact the sender by phone to double check that it is indeed them that have sent it to you. Reputable companies will always have a contact number for you to check this – if you can’t find one, it’s probably bogus.(2)
Top Tip! – If anyone is requesting money, details, or are asking you to follow a link to log in to a personal or business service – always be very wary.
(1) Tip! – Beware of email address spoofing. Even if the sender’s email address looks genuine it could have been spoofed (made to look like it’s come from a genuine email address, when it’s actually come from elsewhere), check through the email carefully and if it’s asking you to do something suspicious, check before you action!
(2) Tip! – Don’t always rely on the contact numbers found within the suspicious email, contact the sender on their main advertised, recognised number to enquire if the contact is genuine. A phone number on a Phishing email could actually put you in direct contact with the spammer!